Valve Finally Fixed the Bug Leaking IPs of Counter Strike Online Players
The gaming community recently suffered from an exploit in Counter-Strike 2 that allowed other users to inject information into Valve’s games and compromise the privacy of other players by exposing their IP addresses. Initially suspected to be a potentially severe Cross Site Scripting (XSS) flaw, the vulnerability turned out to be an HTML injection bug.
The bug was first revealed on a Counter Strike Reddit post under "r/counterstrike":
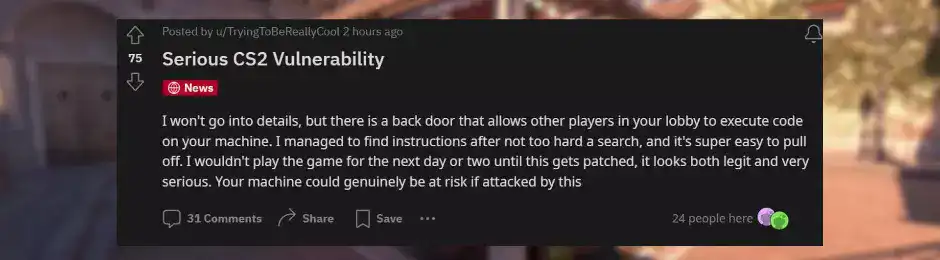
CS2 relies on Valve's Panorama UI, a user interface rich in CSS, HTML, and JavaScript for design layout. The flaw stemmed from the design's configuration of input fields to accept HTML without proper sanitization. When HTML is enabled in these fields, any inputted text will be rendered as HTML on output.
It quickly became very clear that Counter Strike’s online security needs a boost, and fast! Reports flooded in this week as Counter-Strike users discovered the misuse of this HTML injection flaw, particularly in injecting images into the kick voting panel. While some users exploited it for harmless fun, others aimed to obtain the IP addresses of fellow gamers in the match.
By using the <img> tag, malicious users were able to deploy a remote IP logger script, logging the IP addresses of players exposed to the manipulated kick voting panel. These IP addresses could potentially be exploited for malicious activities such as launching Distributed Denial of Service (DDoS) attacks and disrupting players' connections to the match.
To put it into simple words, players would see a kick vote during a Counter Strike match, but in reality, it was an image injected into the game by the hacker. By clicking this image with the intention of voting, players would actually be clicking the maliciously injected image, giving the user their IP address.
With a quick response to the situation, Valve deployed a compact 7MB update to try and fix the vulnerability. Valve deployed a compact 7MB update to fix the vulnerability, ensuring that it properly sanitizes any inputted HTML to a regular string and prevents the rendering of injected HTML in the user interface.
 |
After installing the patch, the game will display injected HTML as a string instead of executing it, thus protecting players from potential privacy breaches. Valve's commitment to addressing vulnerabilities has been a bit lacking lately, putting their dedication to providing a secure gaming environment for Counter-Strike players in doubt with the community, but the security boost they released should at least make it safe to play Counter Strike 2 without losing your private information for now. |
While the update seems to have fixed the exploit, Valve's official confirmation is still nowhere to be seen. Similar vulnerabilities in the past, like a critical bug in Counter-Strike: Global Offensive's Panorama UI, caused chaos among players, creating an expectation that this kind of bug would not be left in the game again.
We’ll keep you updated on Valve’s announcements and any Counter Strike news!

GG Boost, the Best Elo Boosting Experience!
 Deutsch
Deutsch  Français
Français  Español
Español  Português
Português